A cybersecurity project from Northern Arizona University aims to better teach drone technology how to ignore “bad” data from signal jamming, so a drone can continue its mission even in contested areas.
Led by Bertrand Cambou, professor emeritus in the School of Informatics, Computing, and Cyber Systems and CEO and co-founder of High Entropy Security, the cutting-edge technology offers a way to create resilient networks that can deliver information securely in the toughest conditions.
The product is a collaborative effort that includes 80 technologies Cambou’s cybersecurity lab has invented that have been issued patents or have patents pending. It has been funded by the Army Research Lab and Air Force Research Lab for years; now it’s being developed for commercialization with funding from the Regents Grant program, a partnership between the Arizona Board of Regents and the Arizona Office of Defense Innovation.
“In the next six months, we’re using these resources to prepare for commercialization,” Cambou said. “The money that ABOR is spending is to help companies like ours be commercially successful.”
How it works in a military setting
As uncrewed aircraft systems, or drones, become a large part of every country’s military, ways to block that machinery, or capture it and decrypt whatever communication is in it, are also increasing. Right now, Cambou said, a country could deploy 200 drones and only see two succeed in their mission of delivering data securely from one point to another through hostile, or zero-trust, territory. That puts people, plans and resources at risk.
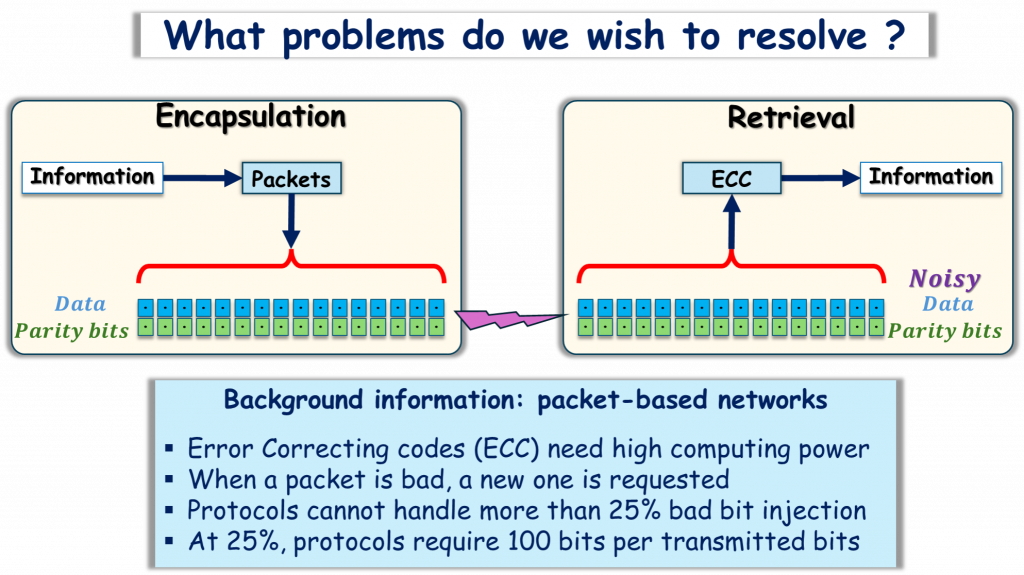
In 2021, NAU’s cybersecurity lab proposed a new technology. Right now, the military sends encrypted data to drones to complete a mission, and enemies use signal jamming to block, disrupt or degrade communication between the drone and the operator. Signal jamming leads to lots of failed missions, Cambou said; the best technology fails when when 20-25% of the data it receives is corrupted. The military needed a way to ensure that drones can both receive key information successfully and keep its own encrypted data safe.
The novel solution, for which NAU has since developed prototypes, is a new mechanism that will allow a drone to have up to 45% bad data and still be able to identify and act on the correct data. The research team, which includes associate professor Michael Gowanlock and undergraduate students from associate research professor Julie Heynssens’ cybersecurity lab, tested the mechanism by introducing noise artificially. You can’t just use signal jamming technology wherever you want, so the artificial noise replicates the effects of signal jamming. They gave directions to a radio-controlled car, increasing the noise as they went. Even with significant noise, the car turned the right way when directed.
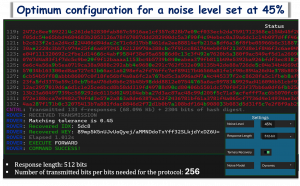
Tests have shown that even with 40% noise in the transmission, the technology sees only 1 bit error per million bits in the encryption keys.
“That is unheard of,” Cambou said.
The technology is also ready for the future.
“Our team has developed software to incorporate all of the latest post-quantum computing algorithms that are standardized by the National Institute of Standards and Technology, so when quantum computing becomes widely available, we’ll be prepared for it,” said Cristy Salanga, NAU’s patent manager and cofounder of High Entropy Security. “It’s ready for quantum. It’ll still be secure then.”
Commercial applications
Enemy signal jamming isn’t the only factor that stops technology from working. Factors as simple and commonplace as poor network coverage on the top of a mountain, a disaster-stricken area or even a crowded farmers market can stop tech like ATMs and credit card machines from working.
“If you’re using a drone, a self-driving or other tech, when you’re outside areas of coverage, you have a dead spot,” Cambou said. “One solution is to use satellite, which is expensive, and the bandwidth is limited. With our technology, we can actually deal with coverage.”
It works, he said, because poor network coverage simply means the data is not clean; there are a lot of bad bits—same as with signal jamming. Their tech recognizes the poor coverage as noise, filters it out and focuses on the direction that is being given. Although the cause of the noise is different, the filtering method is the same.
Read about a new drone project that received ABOR funding for commercialization.
Patents and inventions at NAU
Cambou’s cybersecurity lab is the most prolific inventor in NAU’s history, with more than 100 patents. But this is not the only success at NAU. Led by Salanga, who is program director for the NSF I-Corps, NAU offers support for professors seeking patents for their creations. This allows researchers to develop technology they can then commercialize.
It also makes for profitable collaborations. Some of the codes and methods Cambou used in the development of this technology came from Jeffrey Hoffstein, a mathematician at Brown University who is a leader in the field of cryptography. He is the chief innovation officer for High Entropy Security, and in part due to their partnership, the company has an exclusive licensing agreement with Brown.
Heidi Toth | NAU Communications
(928) 523-8737 | heidi.toth@nau.edu